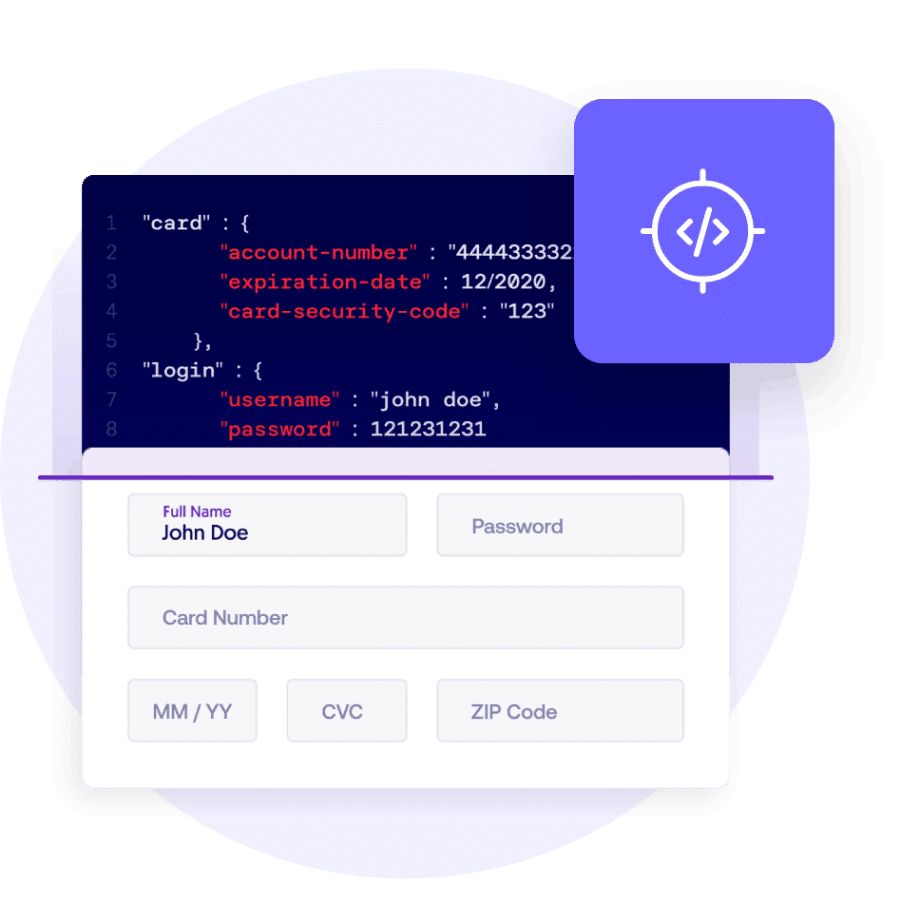
Each interaction a crawler has with your web application is logged and monitored from the security perspective. Inspector undertakes a behavioral analysis and injects logic into each page to gather information that is difficult to collect manually, including:
- The type of data collected by forms.
- The type of data third-party scripts have access to.
- Any first- and third-party scripts that are fingerprinting users and their browsers.
- The types of trackers that are deployed on the page and their activities.
- The existence of any forms or third-party scripts transferring data across national boundaries or to unauthorized entities.
- Any first- and third-party scripts which are being loaded directly into the user’s browser.
- Any first- and third-party scripts that are being sideloaded or chainloaded into the user’s browser.
- The presence of any malicious hosts exfiltrating data.
- Whether any data is being exfiltrated via websockets and the location where it is being exfiltrated.

Still unsure?
Learn how the team at Quickbase uses Inspector to secure their client-side web applications.
Integrate Client-Side Security With Your Existing Technologies and Processes
Inspector’s OpenAPI can integrate with cybersecurity products, application development technologies and ticketing systems, so that Inspector scans results, alerts, and telemetry can be further operationalized. Current integrations include: