If you read the news, you probably know that online sites are increasingly becoming targets of something called Magecart. If you’re scratching your head and asking “Who or what is Magecart?” you’re not alone.
Magecart is a commonly used name for loosely affiliated threat groups that use e-skimming techniques to steal customer data. The term “Magecart” is a portmanteau of the words “Magento” (a popular, open-source, ecommerce software platform) and “shopping cart,” is a type of e-skimming.
How does it work?
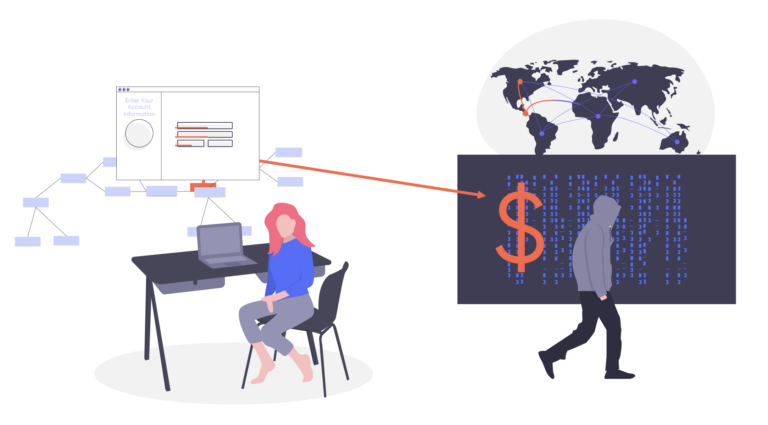
E-skimming attacks, like Magecart, typically follow a simple three-step process to inject skimming code into payment card processing pages of the website.
Step 1—Attackers add malicious code with skimming functions to a third- or fourth-party code (often JavaScript) used by the target website.
Step 2—When a customer visits a website or web page which contains skimming code, the customer’s browser executes the malicious script. The skimming code then steals sensitive information by recording the keystrokes the user types into the form fields. Examples of sensitive information include account credentials, payment card information, and personally identifiable information (PII), like social security numbers.
Step 3—The information the user types into the form fields is sent to the threat actor’s command & control (C2) server for storage and later use.
How to protect against Magecart attacks?
Businesses can reduce the number and impact of Magecart attacks by following these best practices:
Use automated monitoring and inspection: Avoid time-consuming manual code review processes by using automated tools that monitor and scan for Magecart e-skimming code.
Audit web assets: Know your web assets and the type of data they hold.
Maintain safe JavaScript libraries: Don’t use JavaScript from blacklisted libraries and regularly patch and update vulnerable libraries.
Be selective with third-party scripts: Only use third-party JavaScript from reputable sources.
Move security to the left: Make security part of the entire software development lifecycle (SDLC), from start to finish.