In formjacking attacks, hackers, financially motivated threat actors, and other cybercriminals insert malicious code–most often JavaScript–into their targets’ websites. The criminal’s goal is to take over the functionality of the site’s form pages to collect sensitive user information or valuable data. Form pages often include login credentials, names, addresses, phone numbers, credit card information, and other types of personally identifiable information (PII). Criminals sell the data exfiltrated from the forms on the dark web or use it to breach other networks.
Other Names for Formjacking Attacks
Criminals often use formjacking in Magecart attacks. Other names for formjacking attacks include JavaScript skimming, payment skimming, and e-skimming. Tools used in formjacking attacks include JavaScript sniffers.
Industries Most Targeted by Formjacking
Formjacking is most common with organizations that accept online payments from consumers and end users. Formjacking attacks often target businesses operating in the e-commerce, financial services, healthcare, hospitality, and media/entertainment industries. Cryptocurrency and blockchain websites are also increasing becoming targets of formjacking attacks.
How Does Formjacking Work?
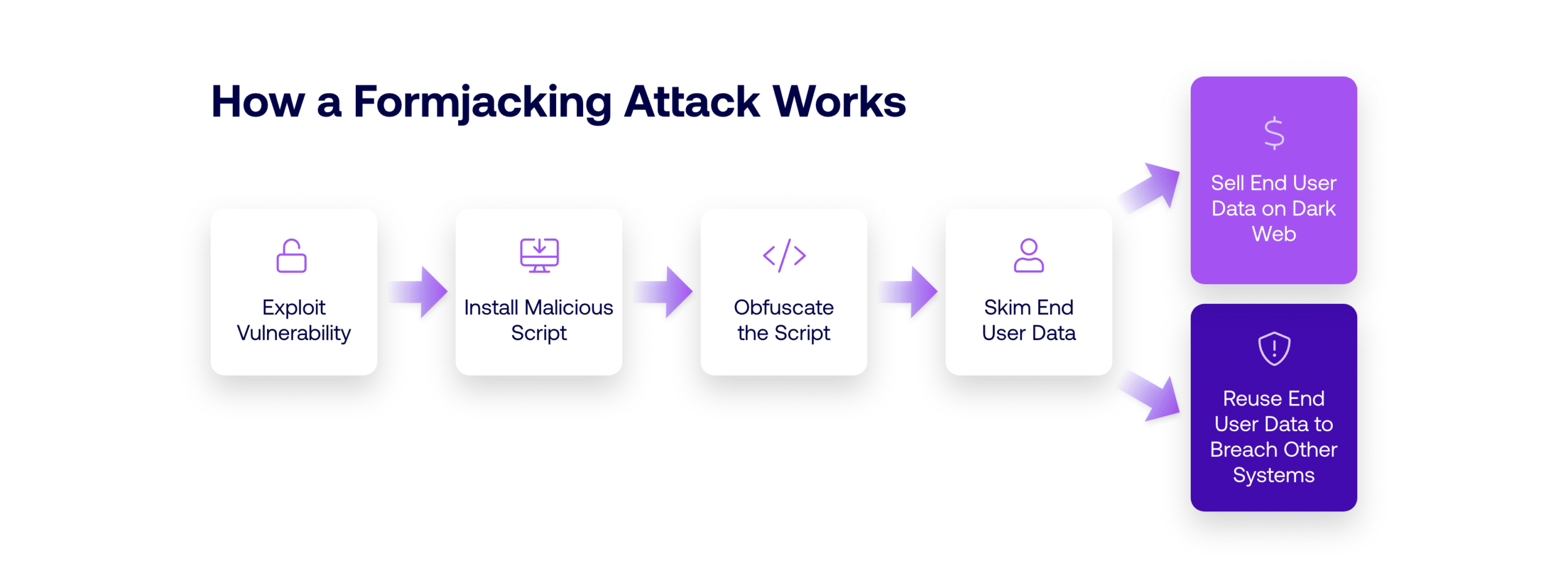
(1) Exploit Vulnerability
Formjacking begins by exploiting a vulnerability related to the web application. The vulnerability could be found in:
- The content management system (CMS).
- The web server’s software or configuration.
- The e-commerce software, for example Magento (which has been a frequent victim of Magecart and formjacking attacks).
- A JavaScript supply chain attack via an open-source or third-party library.
- Access to a system password (often obtained through brute-force hacking or phishing attacks.)
(2) Install Malicious Script
Once the hacker has access, they install the malicious script into the web application. Sometimes the attacker will install the entire script or sometimes they will add a reference to redirect back to where the script is hosted. There are advantages and disadvantages to both techniques. For example, placing the entire script on the target web application reduces the number of connections to remote hosts, but it also makes the script more visible and vulnerable to discovery. Conversely, the attacker may add a small HTML tag to the web application which enables remote malicious script execution. This also gives the attacker the added benefit of modifying and adapting the malicious script as needed without having to directly access the web application. Sometimes this code is stored in legitimate open-source or third-party libraries. However, the attacker risks script discovery and takedown when a recognized and popular library is used.
(3) Obfuscate the Script
Cybercriminals regularly obfuscate malicious script to hide the code and its intent in order to bypass signature string detections. Common types of obfuscation include string obfuscation and Base62 encoding.
(4) Skim End User Data
With the malicious script installed and obfuscated, the attackers now begin the process of stealing data from the forms used by end users to enter personal and financial information. The hacker exfiltrates the data to their own server, making it ready for the final step.
(5) Sell End User Data on the Dark Web or Use It to Breach Other Systems
The goal of a formjacking attack is almost always to make a profit on the stolen information. The threat actor may sell the information on the dark web or use the stolen information, such as login credentials, to engage in further system attacks. All of this is happening with both the business and the end user entirely unaware of the breach.
How Many Websites Are Compromised Each Month With Formjacking Code?
The 2019 Symantec Report FORMJACKING: How Malicious JavaScript Code is Stealing User Data from Thousands of Websites Each Month reports the discovery of 1.5 million formjacking attack during the first quarter of 2019. That is approximately 500,000 formjacking attacks per month on average. The study further notes that, on average, websites compromised with formjacking stayed infected for 46 days.
One of the more prominent formjacking attacks occurred on British Airways in 2018, resulting in a fine of over £20 million pounds (approximately $26 million dollars.) British Airways only discovered the attack when a security researcher alerted them—more than two months after attack initiation.
The increase in e-commerce, particularly with Covid pandemic and the rise in remote work, has likely increased the number of formjacking attacks noticeably since 2019.
Why Is Formjacking Hard to Detect?
For the end user, formjacking is next to impossible to detect, since the business’s SSL certificate and fingerprinting remain intact and operational. Because the attack happens on the client-side—in the front-end JavaScript code—there isn’t any malware downloaded and installed onto the victim’s computer.
For businesses, traditional manual processes, like code reviews, to locate and detect vulnerable, rogue, or malicious scripts are time consuming and labor intensive. Threat actors will also go to great lengths to obfuscate the bad script so it blends into the existing code, making it harder to spot. The attacker may use techniques like typosquatting or homoglyph attacks. The attackers may also masquerade the malicious code as an image to bypass filters.
How to Detect Formjacking
Automated client-side security solutions are the best way to detect formjacking attacks.
- Inspector explores your web assets and reports on any client-side security vulnerabilities. It detects and outlines any areas of concern, then immediately provides specific recommendations that developers, security analysts or application security professionals can use to mitigate the issue.
- PageGuard protects web applications in real-time. It automatically applies security configurations and permissions to every page, ensuring the continuous monitoring of all client-side vulnerabilities, including malware and other malicious third-party scripts. It’s a great way to ensure the protection of your customer across the entirety of their user journey.
- DomainGuard uses automated web application crawling to identify all first- and third-party scripts, digital assets, and the data they can access. It then generates appropriate Content Security Policies based on scanned data and anticipated effectiveness. Customers deploy tailored Content Security Policies at the domain level for easy monitoring, management, version control, and continuous enhancement.
How to Prevent Formjacking
Web application firewalls (WAFs) and subresource integrity (SRI) are traditional ways to help prevent formjacking. These solutions do have limitations. For example, WAFs cannot detect sophisticated malware, manipulated, vulnerable, or sideloaded JavaScript code, or data exfiltration. Further, they cannot protect the browser-level user interface itself.
One of the best ways to prevent formjacking is through automated detection and projection solutions that scan web applications for for anomalies and immediately reporting on any issues.