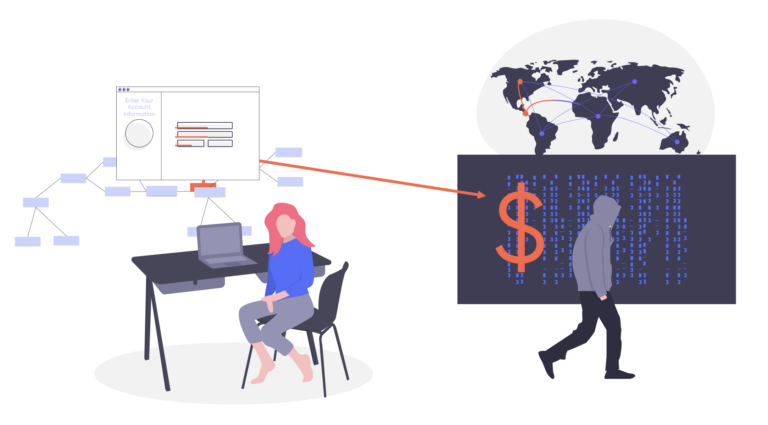
A JavaScript injection attack is a type of attack in which a threat actor injects malicious code directly into the client-side JavasScript. This allows the threat actor to manipulate the website or web application and collect sensitive data, such as personally identifiable information (PII) or payment information. The most common type of JavaScript injection attack is cross-site scripting (XSS).
Who are the targets of these attacks?
Businesses—Any organization that maintains a website that collects sensitive user information, such payment data is at risk of JavaScript injection attack. Industries targeted include retail, entertainment, travel, utility companies, and third-party vendors (such as those working in online advertising or web analytics). The cyber criminals may also target user and administrative credentials in addition to financial or credit card information.
Consumers—Consumer PII, credit card, and financial data are the primary targets of JavaScript injection attacks.
How does an attack work?
During a JavaScript injection attack, malicious code launches when the victim loads the website in their browser. The malicious code can be designed to do many different things, such as capture sensitive information when the user enters data into a form or to steal cookies to be used to impersonate the user for social engineering purposes.
What is the impact of a Javascript injection attack?
Loss of Sensitive Customer Information—A JavaScript injection attack can involve the theft of sensitive PII, including credit card data and name and address. It may also involve authorization cookie theft, which could lead to user impersonation.
Profit loss—JavaScript injection attacks can negatively damage reputation, which can have a harmful impact on profits.
Regulatory and Compliance Issues—Government and industry regulations, such as the Payment Card Industry Data Security Standards (PCI DSS) and the General Data Protection Regulations (GDPR) can subject businesses to lawsuits and fines should business customers be affected by an XSS attack.
What can businesses do to protect against JavaScript injection attacks?
Businesses can reduce the number and impact of JavaScript injection attacks by following these best practices:
Use automated monitoring and inspection: Monitoring and inspection activities are critical, but also time consuming if you don’t have an automated solution to regularly review client-side JavaScript code. A purpose-built solution that automates the process can be a fast and easy way to identify unauthorized script activity that has been injected onto the front end.
Use an advanced, automated Content Security Policy tool: An automated CSP tool can help businesses control their client-side attack surface by deploying and managing Content Security Policies on their web applications. Advanced automated CSP tools identify all your first- and third-party scripts, your digital assets, and the data they can access. The tool then generates appropriate Content Security Policies based on scanned data and anticipated effectiveness. Businesses can fine tune their CSPs at the domain level for easy management, version control, and reporting.
Audit web assets: Inventory your web assets and know the type of data they hold. Look for vulnerable scripts and any signs of manipulation.
Regularly crawl the client side: Regularly conduct deep-dive scans into client-side applications and software to reveal intrusions, behavioral anomalies, and unknown threats.
Block HTML in inputs: By sanitizing user input on the front-end and back-end, malicious code can be blocked from input submission.
Validate form inputs: Limit information that a user enters in a form. For example, require all content to be alphanumeric and block any HTML or tags commonly used in cross-site scripting.
Create safe cookies: Implement cookie rules, such as tying them to a specific IP address, to prevent them from being used in cross-site scripting attacks.