TL;DR
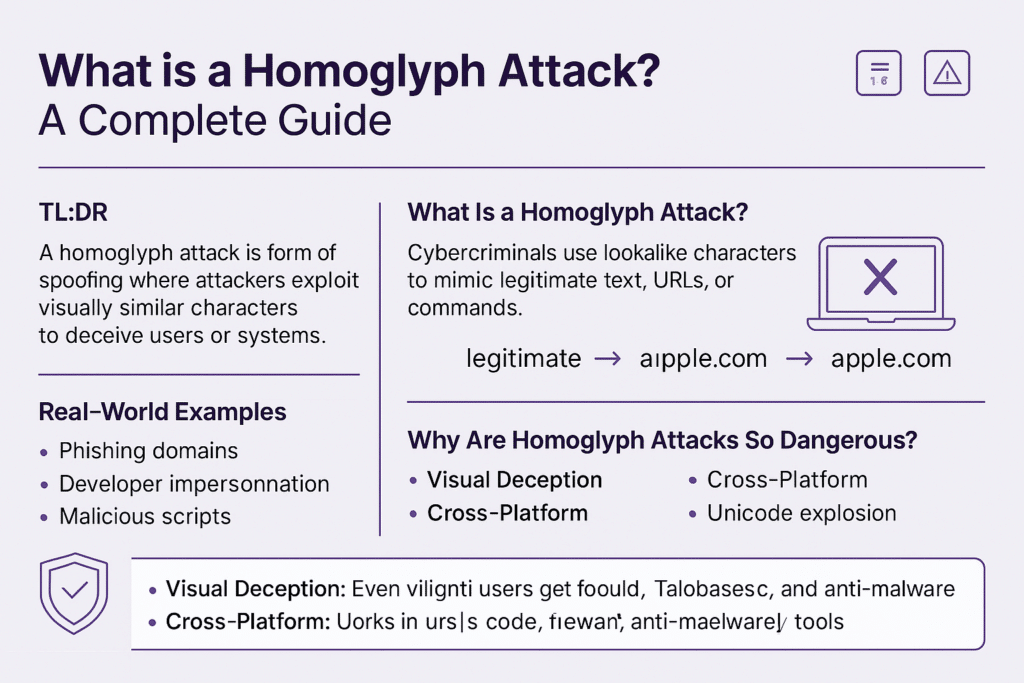
- A homoglyph attack is a form of spoofing where attackers exploit visually similar characters to deceive users or systems.
- These attacks are used in phishing, domain impersonation, and software supply chain intrusions—often with high success rates.
- They’re dangerous because the fake often looks exactly like the real thing.
- Understanding homoglyph threats is critical for application and browser security.
Introduction
Homoglyph attacks might look harmless, but they’re anything but.
This guide is for security engineers, developers, and IT teams tasked with safeguarding users and applications from deceptive threats.
We’ll break down what homoglyph attacks are, how they work, real-world examples, and how to detect and prevent them—especially in JavaScript-heavy and web-facing applications.
What Is a Homoglyph?
A homoglyph is a character that appears nearly identical to another character but comes from a different character set—typically Unicode.
These characters can originate from:
- Different alphabets (e.g., Latin a vs. Cyrillic а)
- Different Unicode symbols (e.g., l vs. ӏ, O vs. Ο)
- Symbols that mimic alphanumeric characters (e.g., @ for a, ! for I)
Homoglyphs are often indistinguishable to the human eye but are technically different to computers, making them perfect tools for deception in digital environments.
What Is a Homoglyph Attack?
A homoglyph attack uses these deceptive characters to spoof legitimate content—like domain names, email addresses, or filenames—to trick users or evade detection systems.
For example:
- Legitimate domain: apple.com
- Spoofed domain: аррӏе.com (with Cyrillic letters)
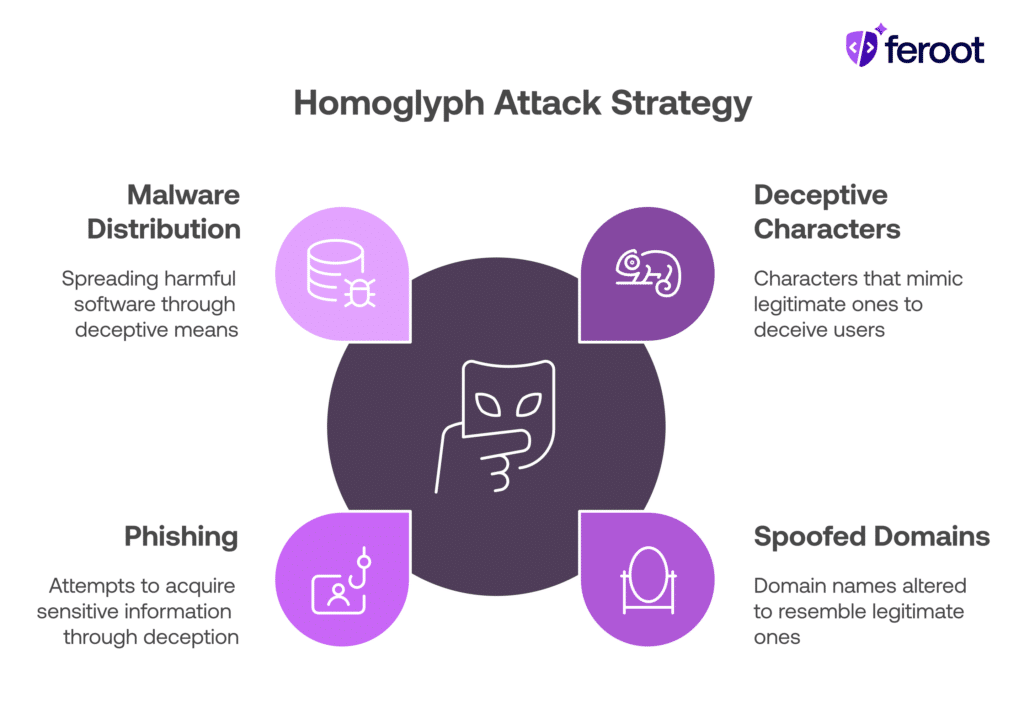
These look identical but resolve to different locations or resources. Attackers use this technique for phishing, malware distribution, and more.
Real-World Examples
1. Phishing Domains
Attackers register domains like gооgle.com (with Cyrillic o’s) to mimic google.com. Victims click links, enter credentials, and fall into traps.
2. Developer Impersonation
A typo in a package name—like numpi vs numpy—could install malware. This is a common software supply chain attack using homoglyphs.
3. Malicious Scripts
JavaScript source files with homoglyph-based names (e.g., scrіpt.js) may bypass integrity checks or appear innocuous in audits.
4. Email Sender Spoofing
A name like admin@goоgle.com can slip past visual inspections in inboxes, especially on mobile devices.
Why Are Homoglyph Attacks So Dangerous?
- Visual Deception: Even vigilant users get fooled. The characters are nearly indistinguishable.
- Cross-Platform: Works in URLs, codebases, command-line interfaces, and emails.
- Unicode Explosion: Thousands of similar-looking glyphs exist in extended Unicode sets.
- Hard to Detect: Traditional spam filters, firewalls, and anti-malware tools may not flag homoglyph-based artifacts.
How to Detect and Prevent Homoglyph Attacks
Detection
- Domain Monitoring Tools: Use scanners that flag suspiciously similar domains.
- Source Code Scanning: Integrate tools that parse Unicode and catch lookalike identifiers.
- Font-Aware Diffing: Visual diff tools help expose character impersonation in code reviews.
Prevention
- Input Sanitization: Normalize Unicode input wherever possible.
- Email and URL Filtering: Block known homoglyph domains via allowlists or fuzz-matching.
- JavaScript Integrity Policies: Enforce strict Subresource Integrity (SRI) and CSP rules.
- Use Punycode for Internationalized Domain Names (IDNs): Browsers will show the actual code, making the trick obvious.
FAQ
What is a homoglyph?
A homoglyph is a character that looks identical or very similar to another, such as O (Latin) and О (Cyrillic).
What is an example of a homoglyph attack?
Registering a domain like facebоok.com (with a Cyrillic “о”) to trick users into thinking it’s facebook.com.
Are homoglyph attacks only in URLs?
No. They appear in file names, email addresses, source code, and even command-line inputs.
How do I protect against homoglyph attacks?
Use input normalization, monitor for lookalike domains, and apply CSP/SRI security policies in web apps.
Why don’t browsers stop these attacks?
Modern browsers mitigate some homoglyph attacks using IDN homograph detection, but many still slip through, especially in multilingual or lesser-known TLDs.