TL;DR
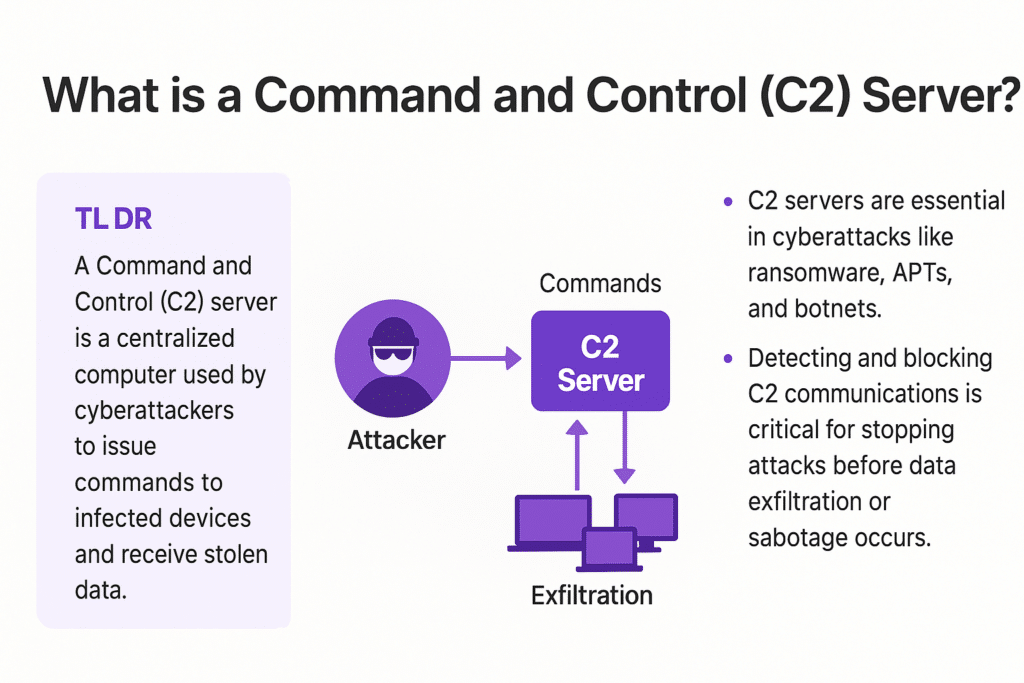
- A Command and Control (C2) server is a centralized computer that cyberattackers use to issue commands to infected devices and receive stolen data.
- C2 servers are essential in cyberattacks like ransomware, APTs, and botnets.
- Detecting and blocking C2 communications is critical for stopping attacks before data exfiltration or sabotage occurs.
Introduction
Who this is for:
Security professionals, developers, and compliance teams responsible for detecting and mitigating malicious network traffic.
Why it matters:
Command and Control infrastructure is the nerve center of most modern cyberattacks. If you can identify or block the C2 connection, you can prevent an entire breach from escalating.
What this guide covers:
- The purpose of C2 servers
- How they operate in real-world attacks
- C2 communication techniques
- Mitigation and detection strategies
What Is a Command and Control Server?
A Command and Control (C2) server is a remote system that attackers use to communicate with compromised endpoints—such as user devices, servers, or cloud workloads. These compromised systems are often called “bots,” “zombies,” or “agents.”
C2 servers send commands like:
- Downloading new malware
- Initiating lateral movement
- Encrypting files (e.g., ransomware)
- Exfiltrating sensitive data
In turn, these systems report back status updates or stolen information. The C2 acts as the control tower for an ongoing cyber operation.
How C2 Servers Work in Cyberattacks
C2 infrastructure appears in many forms of attacks, such as:
- Botnets: Networks of hijacked devices await commands from a C2 to launch DDoS attacks or send spam.
- Ransomware: After infiltrating a network, ransomware often “phones home” to a C2 server to receive an encryption key or exfiltrate data.
- Advanced Persistent Threats (APTs): Nation-state or well-funded attackers use C2s to maintain long-term access, perform reconnaissance, and gradually steal data.
Example:
The SolarWinds Orion breach involved malware that used custom C2 channels to mask communication and stay undetected for months.
C2 Communication Techniques
C2 servers use sophisticated methods to blend into legitimate network traffic and avoid detection:
- HTTP/S tunneling: C2 traffic hides within web requests.
- DNS tunneling: Commands are encoded in DNS queries.
- Fast-flux domains: Rapidly rotating IP addresses to evade blacklists.
- Social media: Some malware retrieves commands from tweets or public posts.
- Encrypted channels: SSL/TLS or custom encryption to bypass content inspection.
These techniques make C2 detection especially difficult using legacy network security tools.
Detecting and Mitigating C2 Threats
Best practices for stopping C2 activity:
1. Use threat intelligence
Integrate with updated feeds of known C2 domains, IPs, and behaviors.
2. Inspect outbound traffic
Monitor for suspicious DNS lookups, encrypted payloads, or unusual beaconing patterns.
3. Segment and isolate
Limit lateral movement with network segmentation and least privilege access.
4. Use behavioral analytics
Tools like EDR, NDR, and XDR can detect command-and-control indicators even in zero-day attacks.
5. Block known TTPs
Use MITRE ATT&CK mappings to block tools, techniques, and procedures (TTPs) associated with C2.
Modern C2 detection also benefits from machine learning models that analyze baseline network behavior. These systems can flag subtle anomalies, even when attackers use encryption or mimic legitimate protocols.
FAQ
What does a C2 server do?
A C2 server remotely controls infected devices, sending instructions and receiving stolen data or updates from the malware.
Are C2 servers always external?
Not always. While most are hosted remotely, some attackers deploy internal (on-premises) C2 servers to bypass perimeter defenses.
How do security tools detect C2 activity?
They monitor outbound traffic, look for suspicious patterns or domains, and use threat intelligence feeds to block known infrastructure.
What happens if you block the C2 server?
The malware loses its command source, often disabling key functionality like file encryption or data exfiltration.
Can HTTPS or DNS over HTTPS (DoH) hide C2 traffic?
Yes. These protocols can encrypt traffic, making it harder for traditional firewalls to inspect or block malicious activity.