Many of us have heard about Magecart and other digital skimming attacks at Macy’s, Ticketmaster, Smith & Wesson and countless other organizations.
Numbers show that Magecart attacks are accelerating—especially during holiday shopping seasons. Macy’s, Ticketmaster, American Cancer Society, P&G’s First Aid Beauty, British Airways, Newegg, and many organizations reported digital skimming breaches over the last few years. It is important to note, however, that while the big names make the news, the majority of Magecart attacks are focused on small- and medium-sized organizations with 50 to 1000 employees.
Ensuring your customers’ data is protected from web skimming criminal groups is becoming an absolute necessity. Let’s take a closer look at Magecart and e-skimming.
What is Magecart?
Magecart is a commonly used name for loosely affiliated groups that use digital skimming or e-skimming techniques to steal customer data.
Magecart web skimming, (aka digital skimming, e-skimming, formjacking) attacks take advantage of browser-level unrestricted access to sensitive data and the lack of control over the JavaScript code executed by a website in the browsers. Magecart attacks steal payment card information, billing data, and other confidential data including user login credentials, which can then be monetized by being used immediately or sold later on the dark web.
What is a Magecart attack?
While prices fluctuate and depend on many variables, the below summary provides a broad picture of commercial models and the monetization of stolen data:
Credit cards
- ~$1,000 – for a credit card with a $15,000 limit
- ~$800 – for a credit card with a $10,000 limit
- ~$450 – for a credit card with a $5,000 limit
- ~$45 – for an average (untested) credit card
Online accounts
- ~$20-$200 – Online payment ID (PayPal, etc)
- ~$20 – Loyalty Accounts
- ~$1-$10 – Online Subscription Services
Other
- ~$1,000 – $2,000 – Passports
- ~$20 – Drivers Licence
- ~$1 – the average price of US SSN
How much does customer data cost on the dark web?
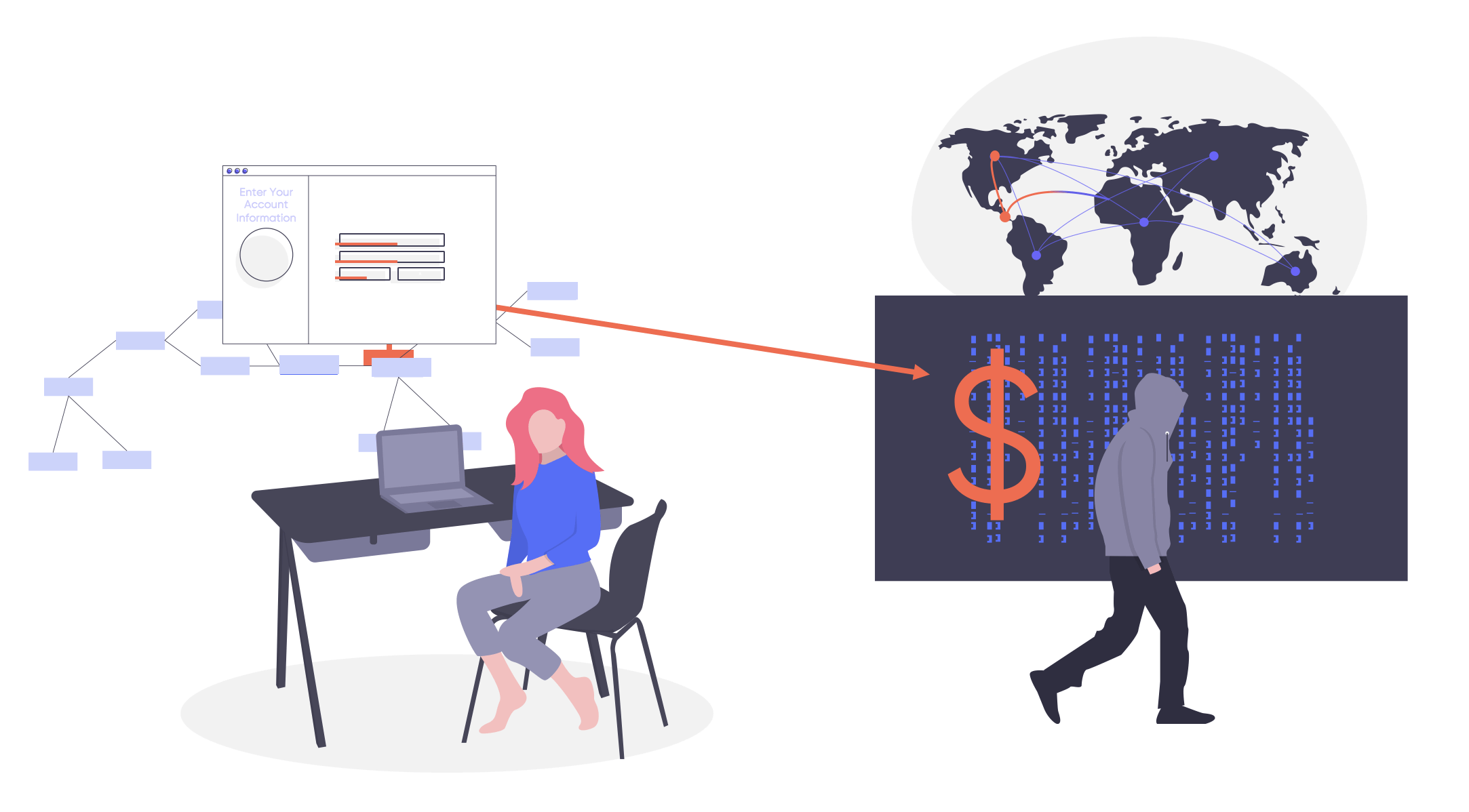
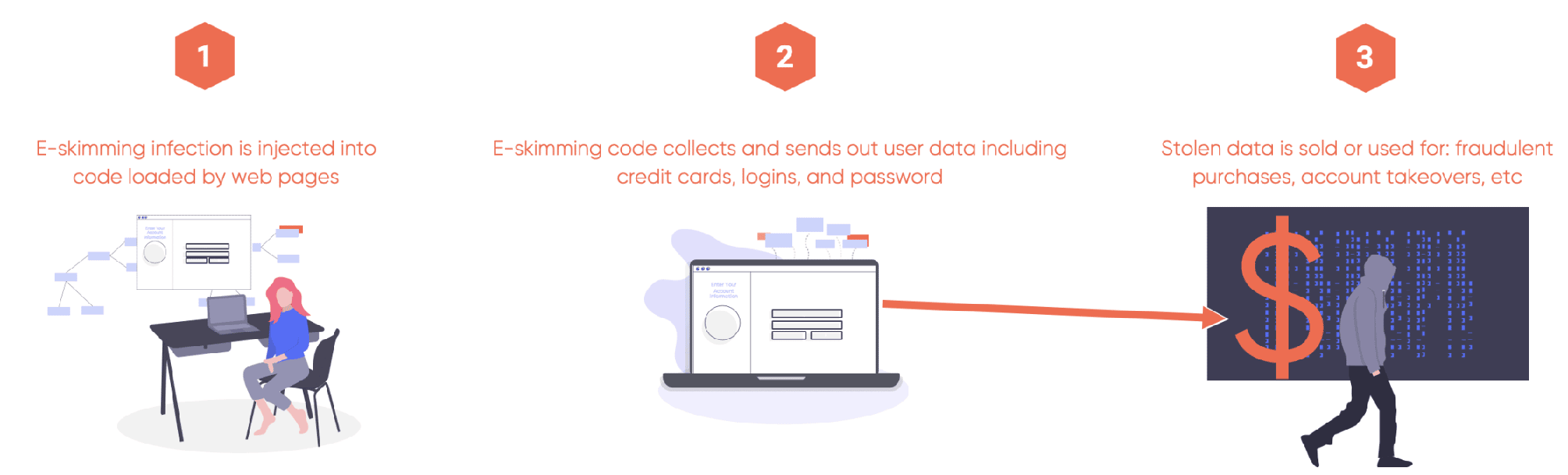
Attackers add skimming code directly or side-load it through first- or third-party scripts that are used by the targeted website. The skimming code is executed by the browser giving the attacker the ability to steal sensitive information, or record keystrokes in form fields, and then send it back to their command and control server.
How does Magecart digital skimming attack work?
As more and more companies conduct business with their customers online, websites that host pages which require customers to enter information are nearly everywhere. It’s now very common to find customer login, credit card payment, and account sign-up pages on almost every businesses website.
Third-party scripts and libraries are often used to implement business-driven functionalities and features like analytics, marketing retargeting, live chat, forms, and shopping carts. Modern web development makes the use of third-party controlled scripts very common and unavoidable. These scripts also leave many organizations vulnerable to skimming attacks.
Why are Magecart breaches becoming more frequent?
E-skimming attacks take place directly inside of the user’s browsers, which is outside the organization’s security perimeter and hence outside of their security operations coverage.
The majority of skimming attacks are discovered after weeks or months in operation. The mean time to detect (MTTD) and mean time to respond (MTTR) on client-side security breaches are astronomical. Victim organizations are responsible for post-breach costs that can reach hundreds of millions of dollars, especially if GDPR fines are involved.
Successful skimming usually relies on one or more weaknesses on either the target website being exploited or third-party code that is loaded by the target website.
When an attacker finds a backdoor, they insert skimming code that will have open access to form fields which process the target data. Skimming code records user input, including recording keystrokes, and then sends it to an external command and control server that is controlled by the attacker.
How to defend?
While no client-side security approach can guarantee 100% security coverage, a well-executed Zero Trust model with detection and prevention of browser-level skimming attacks can help eliminate the majority of Magecart breaches.
Defense in Depth
Protection
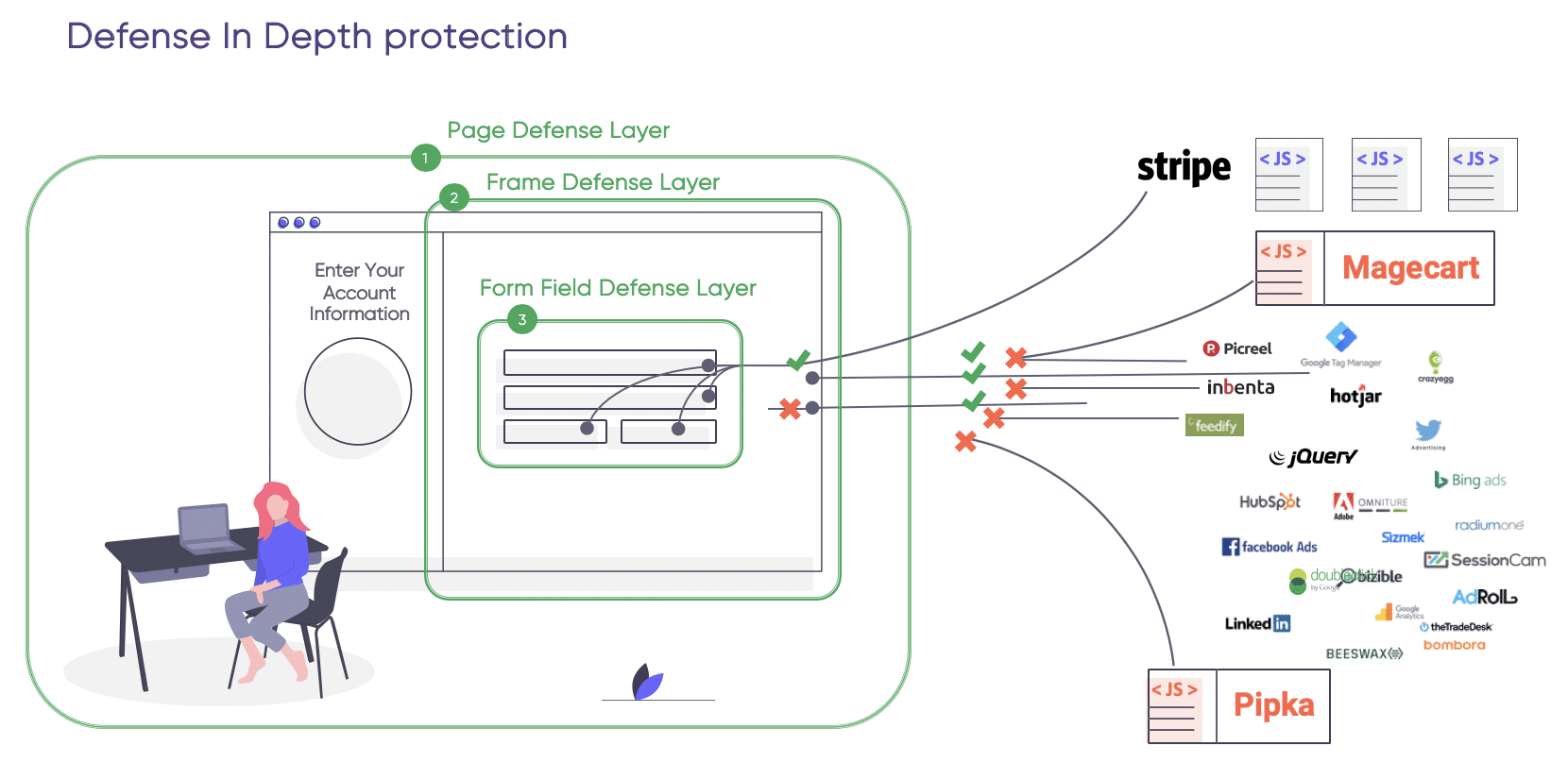
By adopting a Zero Trust approach to both first-party and third-party JavaScript code, you will be able to prevent or significantly minimize skimming threat and their impact. With the Zero Trust model in place, even when any of the code gets infected by a Magecart attack, the skimming script won’t be able to access valuable data.
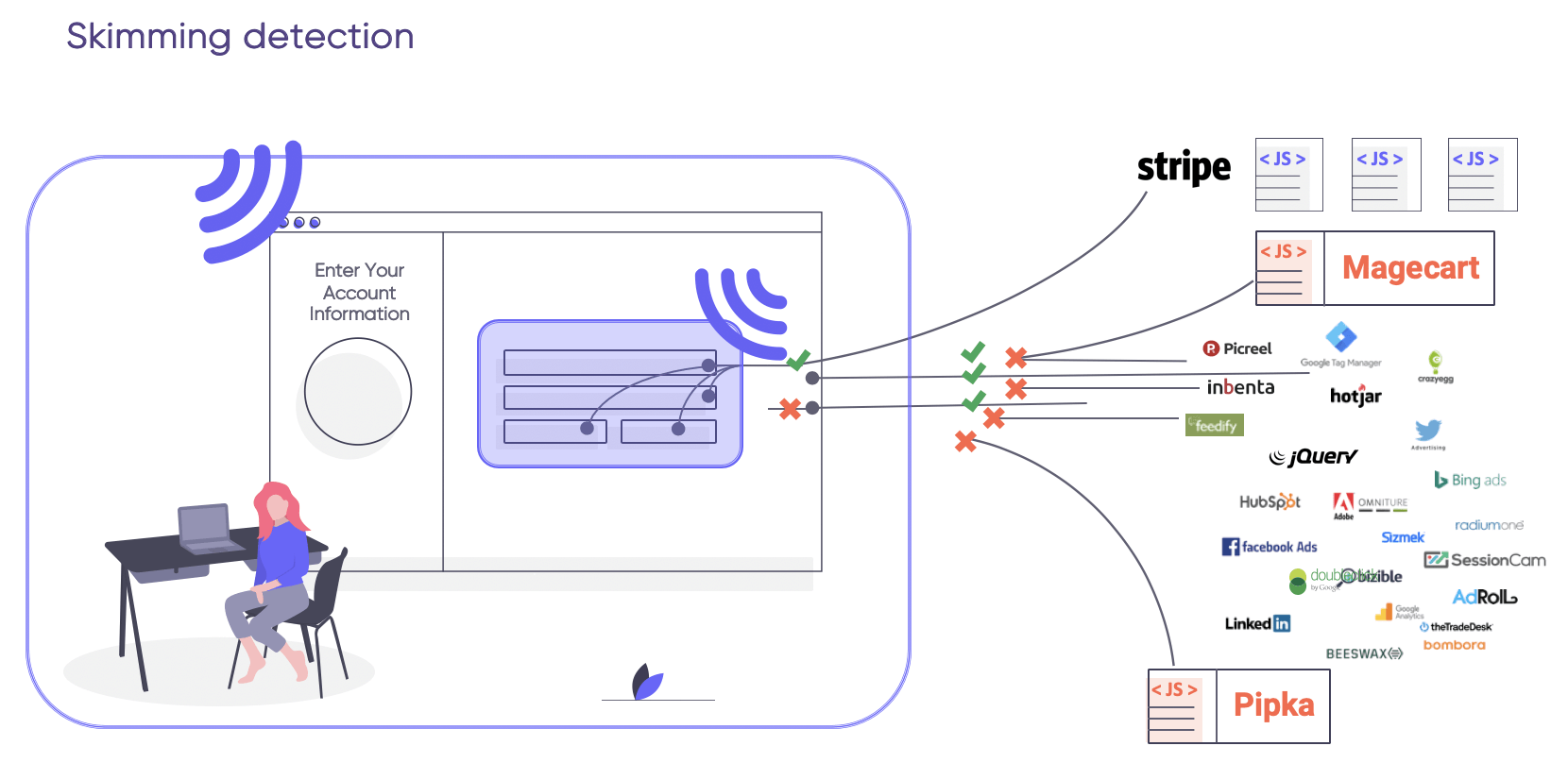
Detection
To detect skimming attacks, commonly exploited code vulnerabilities need to be uncovered. Attackers look for security configuration gaps throughout the web page that processes valuable data.
Magecart prevention-focused security inspection should:
- Determine whether skimming protection safeguards are in place
- Examine whether security access controls present any hazards to customer data
- Enumerate a JavaScript code inventory, data accessed in form fields, and data transferred from user browsers to external destinations
- Observe browser-level activities of code to identify malicious actions
Learn More About Client-Side Security
And if you are interested in automating your SecOps and hardening your skimming defenses? Check out our Inspector and Pageguard solutions that help protect client-side assets. To see these solutions in action, request a demo!


