E-commerce companies are among the businesses most at risk for cyberattacks. High-dollar customer purchases combined with easy-to-hack, JavaScript-based websites are a threat actor’s dream come true. Building a solid e-commerce program means taking some time to understand e-commerce website security, including threats and protective measures.

Security Is Important When Collecting Customer Data
Frustration. Confusion. Turmoil. These are the things that go through the minds of consumers when they find out their credit card information or personal data has been stolen through a website attack. According to recent research, credit card fraud is the most common form of identity theft. In fact, a report by the Federal Trade Commission found that instances of identity theft through credit card fraud increased by 44.6% during 2020.
Where do a large number of credit card thefts begin? You guessed it. On an e-commerce site.
To protect consumers, e-commerce businesses need to make safeguarding customer data, particularly credit card information, a priority. Security starts on the client side or front end of the e-commerce website.
JavaScript and Third-Party Code Are Inherently Hackable
The problems at the heart of modern e-commerce websites often begin and end with several key areas: JavaScript (JS), plugins, and third- and fourth-party code.
While JavaScript, plugins and third-party code from open-source libraries enable common customer engagement features, they are also inherently easy to hack because they contain no built-in security permissions. Over the last few years, with greater numbers of consumers shopping online, e-commerce companies have expanded their investment in the customer digital experience. Unfortunately, JavaScript-based attacks focused on the client side are the unintended consequence of increased e-commerce, as threat actors work to exploit consumer trends.
To fully manage the risk against breaches and attacks, companies must recognize the importance of protecting the client side or front end of their e-commerce websites. This includes everything that the customer sees, such as forms, text, images, stylesheets, and the rest of the user interface, along with anything the customer interacts with, such as what the web application does within the user’s browser.
5 E-commerce Website Threats
To protect against attacks, businesses must recognize the importance of securing the front end or client side. This includes everything that the customer sees, such as text, images, and the rest of the user interface, along with anything the customer interacts with, such as forms and logins.
Five prominent threats faced by e-commerce websites include:
- E-skimming: By injecting malicious code into the client side of a website, threat actors can steal customer data as the customer is engaging with an online form. E-skimming often involves the theft of financial information like credit card data.
- Customer Journey Hijacking: In this type of attack, customers visiting an e-commerce site will see unauthorized pop-up ads and banners designed to divert customers away from the site and onto a different website. Customer journey hijacking begins with malicious JavaScript injections on the client side.
- Cross-site Scripting (XSS): Cross-site scripting (XSS) is a type of client-side code injection attack that allows a threat actor to embed malicious code on the client side of a website. The code then launches when the victim loads the website. The malicious code can be designed to do many different things, such as stealing cookies to be used to impersonate the user for social engineering purposes or capturing sensitive information when the user enters data into a form.
- Cross-site Request Forgery (CSRF or XSRF): Also known as a one-click attack or session riding, cross-site request forgery is a type of cyber attack that forces an end user to execute unwanted actions on a web application in which they’re currently authenticated.
- Formjacking: In formjacking, cyber criminals insert malicious JavaScript code into their targets’ website with the intent of taking over the functionality of a site’s “form” page. With access to the form page, the threat actors can collect any information the customer has entered into the form, including personally identifiable information (PII) and financial data.
Almost 98% of all websites use JavaScript. Another 80% of all websites are believed to use a third-party JS library or web framework for their client-side scripting. So, applying JavaScript security best practices is essential.
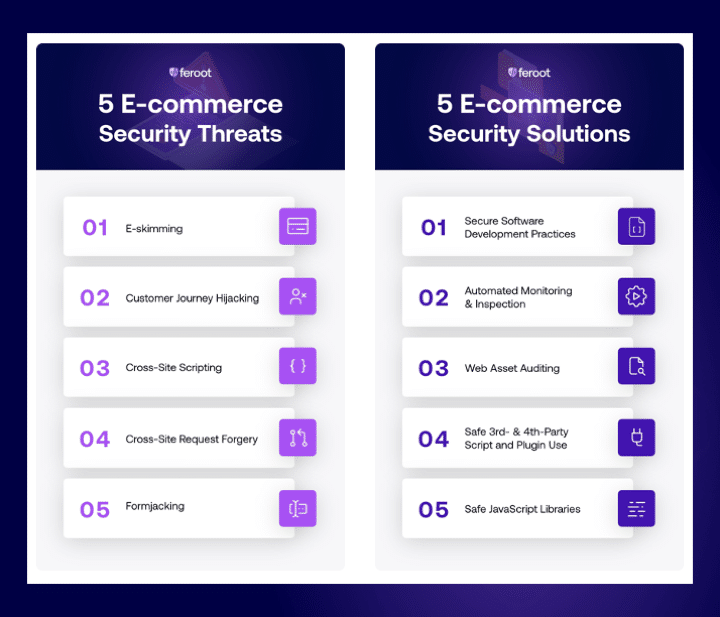
5 Key E-commerce Website Security Solutions
To protect the client side, organizations need to apply critical security processes, tools, and technologies to their web applications. Traditional security tools like web application firewalls (WAFs), policy controls, and threat intelligence simply do not protect the client side.
Client-side security or JavaScript security protects an end user from malicious activity that is occurring on dynamic web pages accessed from the end user’s own device. Improving the security of JavaScript on a website or web application is fairly easy. Here are five simple things businesses can do to implement improved JavaScript security on e-commerce websites:
- Use secure software development practices: Apply best practices that enable the development of more secure application code and aid in the detection and elimination of errors early in the application development process.
- Use automated monitoring and inspection: Monitoring and inspection activities are critical, but also time consuming if they have to be done manually. Implement an automated solution, like Feroot’s Inspector to identify and report on JavaScript web assets and their data access or Pageguard to add security permissions and policies to JavaScript-based applications. A purpose-built solution that automates the process can be a fast and easy way to identify unauthorized script activity.
- Audit your web assets: Know what web assets you own and the type of data they hold and regularly conduct deep-dive scans to reveal intrusions, behavioral anomalies, and unknown threats.
- Be selective with third- and fourth-party scripts, plugins, and tools: Third-party JavaScript and plugins are a great way to avoid the time and money associated with developing your own code, but third-party scripts from open source libraries can also contain vulnerabilities or intentional malicious content. Only use third- and fourth-party scripts, plugins, and tools from recognized, legitimate, and trustworthy sources. Remember to inspect scripts, plugins, and tools for unusual or malicious code.
- Maintain safe JavaScript libraries: Confirm the security of any external libraries by making sure they’re not on any blacklists. Regularly patch and update your libraries and minimize dependence on third-party library sources.
Avoid the Impact of an E-commerce Website Attack
Most companies want to avoid the three biggest impacts of an e-commerce website attack: customer data loss, business reputation damage, and regulatory fines. And it’s important not to forget that unprotected websites that have suspicious code or malware embedded in them can result in Google blocklisting, in which Google lists the website as ‘suspicious’ and displays a message to the user which says: “This site may harm your computer.”
E-commerce Website Security Starts Here
To ensure your users enjoy the best experience possible and that they keep coming back to your site for more, implementing e-commerce website security begins with safe JavaScript. Every customer website engagement is critical to the success of your business. Tools, like PageGuard and Inspector, that protect your website, your customers, and your business, can help you maximize the user experience and minimize the likelihood of an attack or breach. To see client-side security in action, request a demo today.


